
Additionally, it’s recommended to disable scripts and plugins to minimize vulnerabilities. Users navigating this space should exercise caution and be aware of the potential legal consequences tied to specific content and transactions. However, it is crucial to recognize the dual nature of the Dark Web, understanding that while it has legitimate uses, it also harbors risks and associations with unlawful activities. Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions. Dark web monitoring platforms provide secure communication channels for individuals seeking to expose information without fear of retribution. Unlike the direct route taken by conventional browsers, Tor employs a series of encrypted servers known as nodes, chosen randomly, to ensure both user and site anonymity.
Connecting To A VPN Server
Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor. All your device’s internet traffic first goes to the VPN server, then bounces through the Tor Network before ending up at its final destination. A VPN, in combination with Tor, further enhances the user’s security and anonymity. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. If you’re looking for a court case, for example, use your state or country’s public records search.
Types Of Cyber Threats On The Dark Web
Following these practical tips will help you securely explore the Dark Web, reducing risks while protecting your privacy and digital security. Carefully matching your needs to the strengths and weaknesses of each solution ensures optimal privacy, security, and usability. VPNs, proxies, and alternative privacy-focused networks like I2P and Freenet also offer unique advantages. When considering anonymous browsing, Tor isn’t the only option available. Adhering to these methods will help you safely locate legitimate resources while minimizing exposure to potentially dangerous or fraudulent sites on the Dark Web.
- By proactively employing these detailed, actionable security measures, you can confidently mitigate risks and safely utilize the dark web while preserving your privacy and anonymity in 2025.
- When on the dark web, you will need a search engine designed for that environment.
- Due to its hidden nature, the dark web is also famous for the names underground internet and black web.
- The dark web is a subset of the deep web, which includes any online content not visible on normal search engines, such as private databases and personal email accounts.
- As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across.
- Roughly 12,600 volunteer relays power the network as of April 2025, keeping any single observer from tracing both sender and recipient.
Password Managers And Anonymous Email Services: Strengthening Digital Identity Protection
Malwarebytes – all-in-one cybersecurity protection always by your side. While its exact size is unknown, some estimates suggest that it makes up only about 5% of the total internet. The dark web is relatively small compared to the entire internet. When exploring the dark web, it’s crucial to exercise caution, as it’s not devoid of risks. For an additional layer of security, consider using a Virtual Private Network (VPN). You’ll need to follow the same precautions listed in the section above to access the Dark Web safely from your iPhone.
Legitimate Uses Of The Dark Web
The many layers of an onion represent the multiple layers of encryption in the Tor network. In addition, all domains on the Tor network end with the top-level domain .onion (instead of .com). You wouldn’t want your email history available on the surface web and searchable by anyone.

Proton VPN
- The moderators enforce a strict policy against posting links to illegal products or services, so you’re more likely to find safer dark web addresses here.
- No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
- Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn't know exactly what you're doing.
- Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved.
- You will have to use specialized dark web search engines to find .onion sites.
- Dark web encryption allows website owners and users to stay completely anonymous during their engagement.
Accessing the dark web is legal, but engaging in or supporting illegal activities while there is not. It’s simply a part of the internet designed to offer anonymity and privacy. Explore this FAQ section to get answers to some common queries about this hidden part of the internet.
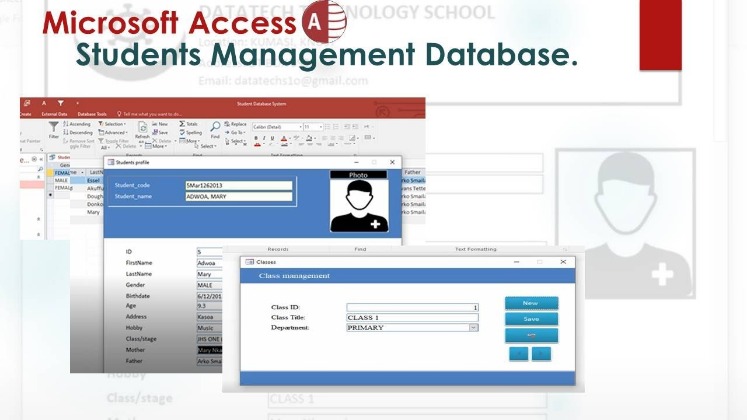
How To Get On The Dark Web In 2025: A Step-by-Step Guide
Content and services on the deep web are accessible through a regular browser. When you search a term (or query) in a web browser, the search engine combs through the database to find relevant results and serves them up on SERPs. Discovered pages are indexed in an extensive database and ranked based on numerous factors. If you’re intrigued and want a firsthand experience, follow this guide to learn how to access the deep web with an anonymizing browser. The hidden web (also known as the deep web or deep net) is the largest part of the internet. Dark web encryption allows website owners and users to stay completely anonymous during their engagement.
It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. It focuses on privacy, censorship resistance, and ensuring free access to content. For instance, your email inbox, online banking account, or a company’s internal database resides in the deep web. Unlike the surface web, you can’t access deep web resources directly through a search engine; they require login credentials or special permissions.
Words Of Caution When Using Dark Web Sites
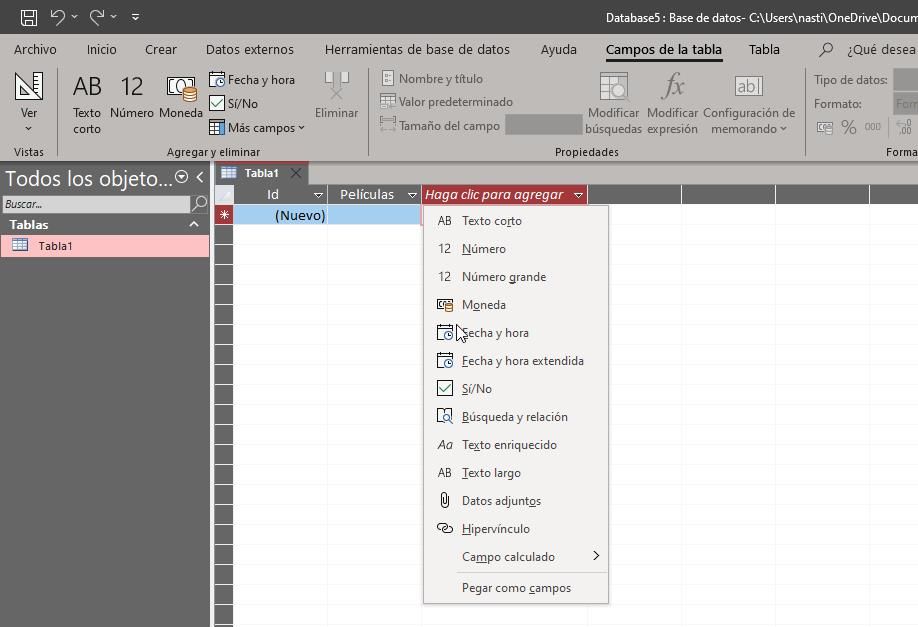
When you connect to the internet using Tor, your data goes through multiple phases of encryption before it’s directed through a random series of servers called ‘nodes’. It’s a free, open-source software using a global network of servers to help you stay anonymous online. Dark web sites are so well-hidden they can’t be accessed with normal browsers such as Chrome, Firefox or Safari. The dark web is a part of the internet hidden from search engines. Perhaps you’ve heard the infamous stories about Silk Road, the online marketplace used to sell illegal drugs with bitcoin behind the veil of the Tor browser.

Navigating The Dark Web Safely
The aim is to reduce your online footprint as much as possible, anonymize your traffic, and disguise your location. Traders cash in on stolen credit card data dumps, initial access points to vulnerable systems, credentials, and intellectual property belonging to companies compromised during cyberattacks. This could include government services to access your records, health care services, members-only areas, intranets, or corporate resources. Websites and pages in the deep web might include password-protected content, private forums, and personalized resources.
Websites on the dark web have .onion addresses, and they operate differently from regular sites. Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com. This adds an extra layer of protection to thwart tracking and monitoring in case the traffic passes through a compromised exit node. A VPN encrypts your traffic before it goes into the Tor network. The most prevalent illicit products are pharmaceutical and recreational drugs, followed by stolen data, online bank account credentials and credit card numbers. Keep in mind that in some regions like China and Russia, it’s illegal to use anonymizers.
SAMA Compliance Download
For one, the VPN can’t see your online activities because of VPN encryption. It encrypts your traffic right away, beneficial if you don’t want your ISP to see that you’re using Tor. You’ll notice that some websites’ loading times are longer when using Tor.



