The dark web is a controversial part of the internet, famous for being a hotbed for illegal and criminal activity. Learn more about our editorial integrity and research process. Dark web monitoring tools are similar to a search engine (like Google) for the dark web. Finally, because the dark web routes all traffic through a series of proxy servers, which are operated by thousands of volunteers around the world, the search process is typically very slow.
- By monitoring forums, marketplaces, and communication channels, security teams can identify emerging threats, compromised credentials, and chatter about planned attacks.
- Knowing about various types of ransomware and common hacks can help you better prepare to spot cybersecurity threats on the dark web.
- Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc.
- Want to stay informed on the latest news in cybersecurity?
- Cybersecurity professionals can leverage the dark web for threat intelligence.
Robotsnet Uses Cookies To Improve Your Experience And To Show You Personalized Ads Privacy Policy
If you exercise due caution and use a combination of the Tor browser and common sense in which sites you access on the dark web, yes, the dark web is safe to use. While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution. There are some websites you can absolutely get in legal trouble for even visiting, so proceed with the utmost caution. Be aware, however, that there are sites for absolutely everything, from the benign to the very illegal. Take a look at the sites that these directories have collected and see what topics interest you. Do not explore random links to websites you aren't aware of or familiar with.
Best Practices For Staying Safe On The Dark Web
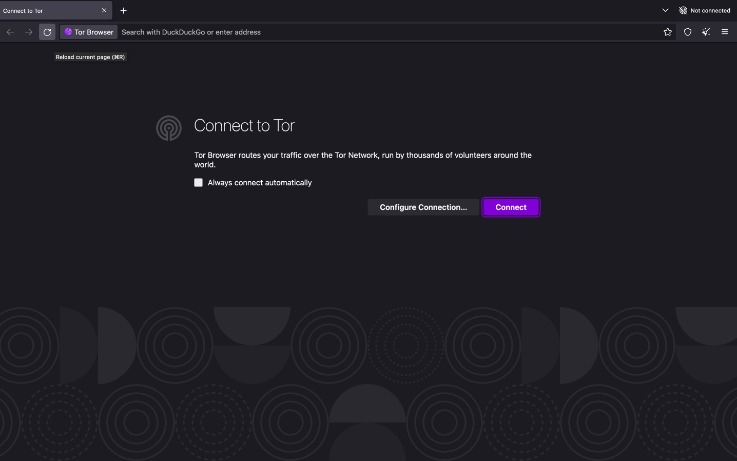
Another great source to find and explore dark web marketplaces or other sections is to visit Reddit’s resourceful forum. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites. If you want to buy something on the dark web, it’s a best practice to create a fake identity. Start the Tor browser by double-clicking on “Start Tor Browser” (for Windows) or “TorBrowser” (for Mac users). MacOS users will need to drag and drop the Tor Browser icon to the Applications folder.
- There are a lot of these sites across the dark web, which is why you have to be extra careful.
- Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and Trojan horses.
- VPN Over Tor is when you first connect to the Tor network and then connect to your VPN.
- However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities.
- Law enforcers can use custom software to infiltrate the dark web and analyze activities.
- The dark web exists to provide users with anonymity and privacy on the internet.
BlackEye Phishing Tool: Features, Installation, And Bes
This secret portion of the Internet is inaccessible via standard search engines and requires specialized software, setups, and Dark Web credentials to reach. We also highlighted the importance of understanding onion websites and navigating the Dark Web safely. The Dark Web carries risks, and it’s important to stay informed and vigilant while navigating this hidden part of the internet. It can be accessed on the Dark Web and offers an alternative to mainstream search engines that collect personal information and track user behavior.

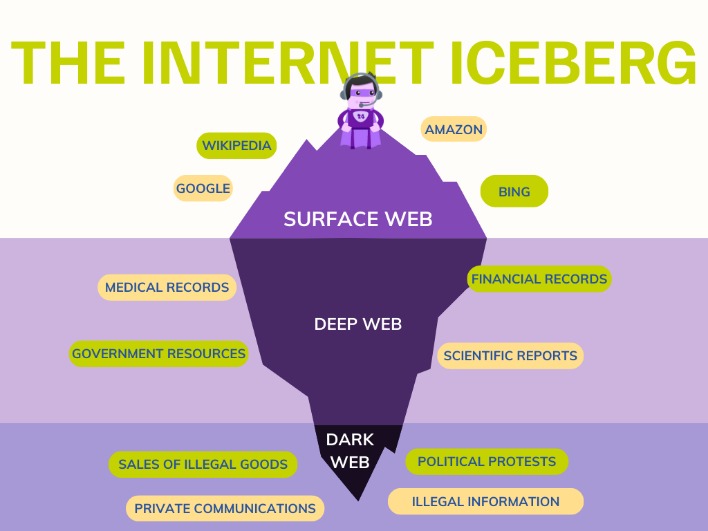
Accessing the dark web also requires knowledge of where to go, since search engines like Google do not index these sites. The dark web is a subset of the deep web that is intentionally hidden and accessible only through specialized anonymity-preserving software, such as Tor or I2P. Although not visible to search engines, these resources are typically legitimate and require credentials, subscriptions, or specific queries to access. The deep web refers to all web content that is not indexed by search engines.
Invest In A VPN
This is where Tor websites are located, deemed the ‘dark web,’ and can only be accessed by an anonymous browser. The dark web isn’t only about illegal activities; its primary purpose is to provide maximum anonymity by making your connection private online through encrypted servers. This article explores a step-by-step guide accessing accessing the dark web safely and anonymously for legitimate purposes. This hidden part of the web carries several illegal activities, including drug and weapon dealing, pornography, private data, and more. Staying off the dark web, if possible, is crucial for several reasons, primarily due to the inherent risks and illegal activities that dominate this hidden part of the internet.
Step 3: Launch Tor And Connect
If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node. Because it’s not as safe as Tor over VPN. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN.
What Is Deep Web: Complete Guide 2025
That information can include checking and credit card account numbers, social security numbers, and other sensitive information. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news. While some studies have claimed that illegal Bitcoin activity is as high as 44%.

Darknet markets facilitate transactions for illegal goods and services. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web. There are multiple search engines on the dark web that can help you find what you’re looking for. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better.
Bad actors can compromise nodes, with exit nodes being of particular concern. Because the Tor network is run by volunteers, there’s also little in the way of accountability. It connects you to a network of servers rather than a particular server. That said, it’s worth noting that the Tor browser is not the same as a VPN. Tor’s anonymity function is used by everyone from human rights workers and journalists through to drug and arms dealers. This makes it very difficult to trace the original users’ identity.
They contain text and images, clickable content, site navigation buttons, and so on. The dark web can only be accessed using a special browser called Tor. Within the deep web is another part of the internet called the dark web. Some commentators use the term ‘the deep web’ incorrectly when they really mean ‘the dark web’. Your email inbox, online banking and Google Drive folders are undiscoverable via a web browser.

The hidden nature of the dark web has earned it the nicknames black web and underground internet. Then, use data breach monitoring software to help find out if your personal data has leaked onto the dark web. The “onion routing” technology underpinning the dark web was developed by researchers at the U.S. If you encounter this content label online, report it to the authorities immediately.
For a legal perspective, refer to The Electronic Frontier Foundation (EFF) which provides resources on internet privacy rights. Install Avast SecureLine VPN for iOS to protect your privacy and keep your data from falling into the wrong hands. Install Avast SecureLine VPN for Android to protect your privacy and keep your data from falling into the wrong hands. Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands.

If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. Although the underground internet world is rife with everything bad, it also hosts positive elements. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article). Install AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web. Download AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web.



