It encrypts your connection and hides your IP address from third parties, adding an extra layer of security. It’s free, open-source software, specifically designed to protect user anonymity through layered encryption. On the other hand, the dark web is a smaller section of the deep web that requires special software or configuration, like the Tor browser, to access. It is essential to verify the links posted on it before you visit any, always. Tunnels is ideal for those who want secure, private conversations online.
But finding reputable onion links and dark web websites can be a challenge. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. However, no matter how much you try to stick to legal websites, you can still land on illegal or highly disturbing content. Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. With the onion browser, you can access ordinary HTTPS websites on the web.
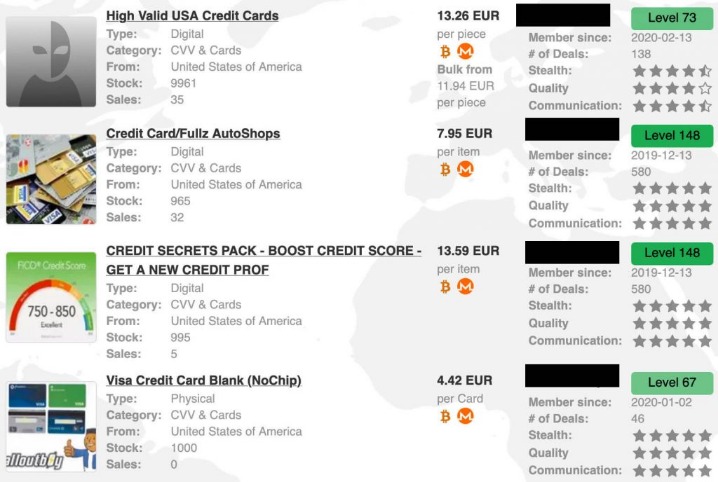
Since its inception, the market has catered to criminals looking for high-quality counterfeit items, such as fake IDs, passports, and branded luxury goods. One of the distinguishing features of Fresh Tools Market is its focus on providing up-to-date, freshly obtained tools and credentials. Fresh Tools Market has become a go-to platform for cybercriminals seeking access to malicious software such as keyloggers, Remote Access Trojans (RATs), and ransomware-as-a-service. FreshTools, founded in 2019, specializes in selling stolen account credentials and data, particularly webmail, RDPs (Remote Desktop Protocols), and cPanels.
Dark Search
Before attempting to use it, learn more about the dark web and make sure you know how to stay safe on dark web websites. In the image above, (a) is the surface web, which includes publicly visible websites like blogs, shopping sites, and news sites. The dark web is the unregulated part of the deep web, which encompasses all parts of the web not indexed by search engines. Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes. The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy.
Is It Illegal To Use The Tor Browser?
It is often grouped with search tools because it organizes links by topic, such as forums, marketplaces, and privacy tools. While you can access it through Tor for privacy, it doesn’t index .onion websites. Their crawlers run through the Tor network, allowing them to load .onion websites anonymously.
Dark Web News And Media
Privacy advocates frown upon it because of the way it harvests data and profiles users. BBC News is still around, though, along with a handful of others, ensuring that users can access impartial information, wherever they are in the world. Creating a Proton Mail and accessing it via the Dark Web creates added anonymity for the user, which is useful for ensuring greater levels of privacy. As a result, it is probably a good idea to double-check and verify any onion links you find using a secondary source such as Onion Links or DarkWebPug. In addition, it is worth noting that users should not blindly trust links on the Hidden Wiki because this is a community resource that anybody can update, and some of the links are malicious.
What Is The Dark Web & How To Stay Safe
- Transactions are made using cryptocurrencies to maintain anonymity.
- Safe darknet shopping requires following best practices for OPSEC, package handling, and risk management.
- However, some significant security risks still remain because the dark web is not regulated.
- Keep reading for a rundown of the best dark links you might want to check out.
- The kill switch feature also ensures your real IP stays hidden if your connection drops.
Some of the most valuable conversations and innovations happen away from public search engines. Learning how to search darkweb content safely starts with understanding that not all parts of the dark web are malicious. Using Bitcoin-only markets because Monero seems complicated, or avoiding PGP because it's inconvenient, compromises security. When that market closes, users scramble to find alternatives. Phishing sites steal more cryptocurrency than any other attack vector.
Why Is A VPN Important When Accessing The Dark Web?
You can access it on the clear net or by using Tor. Imperial Library is a public database of scanned books. The only thing is, you can’t just access Riseup, you need an invitation code to set up an account. The platform owners won’t be able to see your data either.
How To Stay Safe On The Dark Web
You can archive any site you want, or retrieve historical records wherever available. Browsing ProPublica’s work through its .onion site works well, and the site’s very existence is a big win for privacy and free speech. The first online publication that won a Pulitzer became the first major publication with a .onion address. TorLinks serves as a backup or secondary directory site to the popular Hidden Wiki.
Riseup is an invite-only email and communications service that doesn’t hold onto any of the data you generate when you use it. However, The Wayback Machine allows website owners to block their sites from being archived, while archive.today does not. Although ProtonMail also exists on the clear web, accessing it via Tor provides an extra layer of privacy if you don’t want to leave a trace of you even using ProtonMail. The service retains no copies of any data that passes through a ProtonMail account. ProtonMail is an email service that uses end-to-end encryption, making your email accessible to you and only you. The software requires two-factor authentication to receive what’s been uploaded by the whistleblower and allows two-way communication between the anonymous contact and the media outlet.

Just keep things minimal and metadata-free. They are critical for anyone uploading files or hosting content on the dark web. These tools erase embedded information in your files that could expose your device or location. Always use escrow, PGP encryption, and protect your metadata. These tools make trading or investing completely anonymous—a huge win for privacy lovers in 2026. If you’re not using a VPN or secure browser, you’re not anonymous.

Yes, most of these marketplaces allow vendors to list their products or services. Escrow services are intermediaries between buyers and sellers in a marketplace. Yes, these markets prioritize user security with advanced measures like encryption, PGP key authentication, and escrow systems. Additionally, DrugHub provides vendors with access to private mirrors, adding an extra layer of security against unauthorized access. By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved.
Riseup’s suite of services includes encrypted email, mailing lists, VPN (Virtual Private Network) services, and collaborative tools, all designed with a focus on security and ease of use for its user base. This information is invaluable for developers, researchers, and users interested in the technical and sociological aspects of the Tor network. It collates and presents data on a wide range of metrics, including but not limited to the number of active users, the distribution of relay countries, bandwidth statistics, and the overall growth or contraction of the network. Tor Metrics is an essential analytical tool and service that offers comprehensive insights into the Tor network, an open-source project designed to enhance internet privacy and security. Users have access to settings that allow them to control search parameters and privacy settings, further enhancing the personal security and customization of the search process.
Dark websites use .onion domains, which are only accessible via a tool like the Tor browser. The dark web operates on encrypted networks and uses protocols that traditional search engines can't access. Dark web search engines are specialized tools that allow users to search the dark and deep web.

Initially known as DaMaGeLaB, the forum rebranded in 2018 after the arrest of one of its administrators. Some are geared towards academic, professional, or hobbyist communities, while others are havens for illegal activities. Dark web forums, in particular, are notorious for hosting discussions on illicit topics.
Their tools often spread through phishing campaigns or compromised software downloads, enabling crimes such as identity theft. However, rivalries over dark web marketplaces could also lead to turf wars, disrupting their operations and creating new risks for businesses. In 2025, state-sponsored actors are expected to continue using the dark web for politically motivated cyberattacks.
This commitment underlines the search engine's dedication to providing a safe and constructive environment for dark web exploration. This approach not only ensures a high degree of privacy for its users but also fosters a listening environment where music is appreciated in its purest form, without algorithmic influence. Founded with the intent to leverage the anonymity of the deep web, Deep Web Radio allows both broadcasters and listeners to engage with music away from the surveillance and commercial influences that pervade many online platforms. This transparency was instrumental in demystifying the operations of Bitcoin for a broader audience, showcasing the technology's potential for secure, decentralized transactions without the need for traditional financial intermediaries. The platform started primarily as a blockchain explorer, allowing users to view and analyze transactions on the Bitcoin blockchain in real-time. Furthermore, the service does not require user registration, allowing anyone to archive and access snapshots anonymously.



