
A user could have as many addresses as they chose to create with one of the many wallet programs that managed their coins—like a bank that allows you to spread your wealth across as many accounts as you liked, creating new ones with a mouse click. She could see, for instance, the nearly 1 million bitcoins that were mined by Satoshi in the early days of the cryptocurrency, before others started using it, as well as the first transaction ever made when Satoshi sent 10 coins as a test to the early Bitcoin developer Hal Finney in January 2009. Yes, identities behind those payments were obscured by pseudonymous addresses, long strings of between 26 and 35 characters.
How Law Enforcement Is Disrupting Ransomware Gangs
Badawi et al. (2022) use a list of approximately 700 search terms for BG sites on the clear web. One of the decisions in the study is how to search for BG sites. Therefore, our process for locating advertisements starts with selecting recent BG sites. The second approach, which we have chosen, begins by identifying the names of BG sites and then searching the dark and clear web for those specific websites. There are two main ways to find advertisements for BG sites on the dark web.
Cryptocurrency is commonly used on darknet markets due to its perceived anonymity and its ease and efficiency for transferring funds across international borders. Each transaction contains data such as the payment amount sender and recipient addresses. Therefore, blockchain addresses and Bitcoin are pseudonymous rather than anonymous. It contains all the transactions ever made and records the sender’s and receiver’s addresses, as well as the amount of Bitcoin.

Cryptocurrency Crimes On The Dark Web
- Efforts to combat ransomware attacks involving cryptocurrencies are underway, with collaborations between law enforcement agencies, cybersecurity firms, and cryptocurrency exchanges.
- Bitcoin has made it possible for individuals to conduct transactions anonymously and securely.
- Then, we investigate both market star-graphs and user-to-user networks, and highlight the importance of a new class of users, namely ‘multihomers’, who operate on multiple marketplaces concurrently.
- This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites.
The results further support the recent efforts of law enforcement agencies to focus on individual sellers43,44,45, as well as, more recently, also buyers46,47. For example, in some cases, a seller in a given market may behave as a buyer in a second market or in the U2U network. For instance, there may be sellers that make a small amount of transactions, or spend more than receive, which we would classify as buyers. There is a gray zone in which some sellers and buyers may not be easily distinguishable in transaction networks. We showed that a small fraction of traders is responsible for a large fraction of the trading volume, and by analysing the networks of buyers and sellers, we found different resilience regimes.
They sometimes don’t require an ID and can pay in cash — you don’t even need a Bitcoin wallet. Make sure to use a service that keeps no records of any mixing transactions. Since the platforms do not hold any fiat, they don’t require users to go through a KYC process. Note that financial platforms tend to change policies often, and by the time you read this article, these, too, may change their requirements. Ensure these services use the latest encryption standards and do not log your IP address or other information. A VPN service will hide your IP address, which is one effective way to protect your privacy, especially when accessing specific internet services.
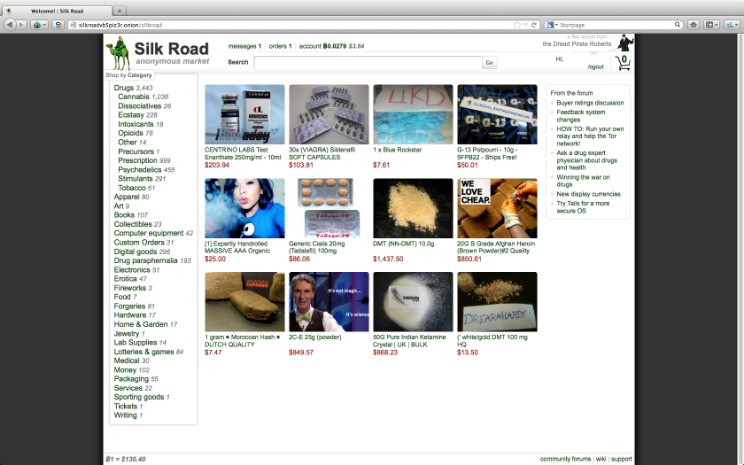
Silk Road Dark Web: History And How It Shaped Online Crime
Many people see hacked information and stolen card data being sold on the dark web. The dark web also helps individuals communicate about or sell illegal items such as weapons, drugs, malware, etc. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. Other sites explicitly block search engines from identifying them.

The Hidden Wiki

And particularly, investigators gained insight into the platform’s users when they seized Son’s server. Son and many Welcome to Video users were sloppy enough that investigators could connect them to their dark web activity with relative ease. He is charged with one count each of concealment money laundering and engaging in a financial transaction using illegally obtained funds. Dash and Monero, a cryptocurrency with strong privacy credentials, emerged as favorites, while bitcoin and its offshoot bitcoin cash were ranked last. Silk Road had become a popular market, one of the first real places where Bitcoin could be used as money.
As a result, scammers are at greater risk of attracting the attention of law enforcement, although they also benefit from a larger audience and easier accessibility for users. The clear web is generally easy to access, with authorities actively monitoring illegal activity. Cryptocurrency scams exploit the complexity of blockchain technology to deceive victims, with the Bitcoin generator (BG) scam being a notable example. On the dark web, the top three clusters of crypto addresses account for 35% of the total revenue.
Are All Bitcoins Transactions On The Dark Web Illegal?
- A top-of-the-line VPN network that ensures maximum security while accessing dark sites online.
- Online cryptocurrency trading markets (exchanges) have varying levels of compliance with regulations regarding financial transactions.
- Users should exercise caution when choosing a dark web bitcoin exchange and conduct thorough research before engaging in any transactions.
- It underscores the need for robust cybersecurity measures, timely software updates, and user education to prevent such attacks from occurring in the first place.
He was charged with money laundering, computer hacking and trafficking fraudulent ID documents, as well as allegedly paying to have two people murdered and other narcotics charges. Ulbricht appeared to have libertarian leanings that shone through in his creation of the Silk Road, creating a marketplace that existed without government oversight. Thanks to Bitcoin, the Silk Road emerged as the major market in the dark web because it had adopted an unregulated and borderless payment system.

“Somewhere in the back of my mind was this idea,” says Meiklejohn, “the idea of following the money.” Over the years that followed, the elder Meiklejohn would make her career taking on contractors who were bilking the city government out of tax dollars—bribing government staffers to choose overpriced school food or street-paving services—or else banks colluding to sell low-performing investments to the city’s financiers. Meiklejohn was still in elementary school, but it was take-your-daughter-to-work day, and Meiklejohn’s mother was a federal prosecutor.
Challenges For Law Enforcement
She credited her intuitive acceptance of that principle to her years as a teenager who kept to herself, trying to maintain her own privacy in a Manhattan apartment, with a federal prosecutor for a mother. More tantalizing than even the story of Alice Kober’s work on Linear B, for Meiklejohn, was the fact that no one had been able to decipher Linear A, even after a century of study. One of the first websites Meiklejohn remembers visiting on the nascent World Wide Web was a GeoCities page devoted to deciphering the Kryptos sculpture on the campus of the CIA, whose copper, ribbonlike surface contained four coded messages that even the cryptanalysts at Langley hadn’t been able to crack. On road trips, in airports, or any other time the small-for-her-age, hyper-inquisitive girl needed to be distracted, her mother would hand her a book of puzzles.
It is both a new currency and uses different methods than traditional ones to complete and confirm transactions. In many cases, countries do not allow citizens to go on certain websites. Other people might not be in a position to use conventional e-commerce sites in their country. But just because it was made for illegal purposes does not mean that it can be used to buy things legally.
Hydra Marketplace Takedown
Hence we do not distinguish multisellers by the number of markets in which they operate. In particular, multihomers that are sellers in multiple markets are multisellers, and similarly for buyers we have the multibuyers. To analyse the connectivity of the whole ecosystem, i.e., how markets are connected with each other, we consider sellers and buyers that are simultaneously active on multiple platforms. We assess the strength of a market’s dominance by the market share (i.e., the market revenue divided by the sum of the revenues of all markets) and by the length of the time interval the market remains dominant, as shown in Fig. Moreover, we find a change of trend between the seller and the buyer median net income time series which reflects the dominance of markets, as detailed in the next section. Notably, the number of buyers and sellers significantly drops after the operation Bayonet in the last quarter of 2017, which shut down AlphaBay and Hansa markets, causing a major shock in the ecosystem34.
Accessing Onion Sites On Android
Whistleblowers, for instance, can find the anonymity available through the dark web valuable when working with the FBI or another law enforcement organization. Note that just because a site or service is running on an encrypted, hidden network does not necessarily mean that it is illegal or dubious. Our market features a vast selection of goods and services, all designed to protect your privacy and ensure safe transactions.
That morning, Meiklejohn and her mother had taken the subway together, all the way from their Upper West Side apartment near the American Museum of Natural History to the federal building at Foley Square, across from the city’s intimidating, stone-columned courthouses. Meiklejohn’s hundreds of purchases, bets, and seemingly meaningless movements of money were not, in fact, signs of a psychotic break. If you buy something using links in our stories, we may earn a commission.



